A penetration test (pen test) consists of a simulated cyberattack by a security professional to determine whether the tester can access a target through device vulnerabilities. Recall from the “Edge Security in an Insecure World” blog that the network interface for an internet-connected device forms a large portion of its attack surface. The edge-device network interface exposes a number of network ports that present unique protocols to the internet. Each of these ports is a potential entry point for a hacker—for example, the HTTP protocol exposed on port 80 or 8080. Understanding the protocol (and version) exposed on a given port provides a wealth of information to the hacker.

Pen Test Process
As a simulation of a hacking event, the pen test follows a process similar to that of a would-be hacker. Below is a simple process for attempting to penetrate a system on a network. The test process consists of:
- Target Selection
- Vulnerability Detection
- Exploit Matching
- Exploit Attempt
For target selection, this is simply the authorized device under test. The target is then probed by a vulnerability detector, such as a port-scanner, to assess the entry points to the device along with other information about these entry points (protocol, version, etc.). Next is the identification of potential exploits for those entry points with an attempt of the exploit as the final step (Figure 1). This process ignores custom exploit development, which is a considerably more complex process.
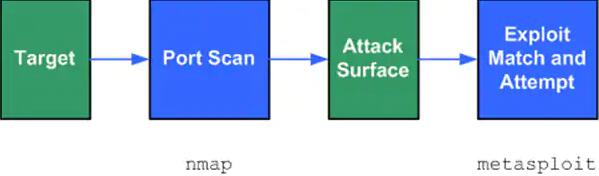
Figure 1: Diagram of the Penetration Testing Process. (Source: Author)
Port Scanning
To identify potential vulnerabilities on a device, one of the simplest approaches is the port scanner. A port scanner is an application that scans a device for open ports, and then through the port numbers associated with those ports, identifies the accessible network services. Because a port number can represent numbers in the range of 1 to 65535, the port scan can be a time-consuming process.
Port scans are performed in several ways, but in the simplest case, the port scanner attempts to connect to ports on the device. If the device confirms the connection request, commonly called a three-way handshake for TCP, then the port is open. Otherwise, the port is closed or blocked.
The pen test can usually identify the network service using the port number. For example, if the port scanner finds an open port at port 80 or 8080, then the HTTP protocol is available.
The details of the underlying packets exchanged between the device and port scanner also provide a wealth of information. The tester can use information about how a particular device configures parameters of the protocol to identify the operating system (OS) or protocol stack in a process called device fingerprinting.
Figure 2 provides the sample output of the Network Mapper (NMAP) port scanner utility. This particular request uses the stealth SYN packet method and requests service information for open ports against the network device 192.168.1.4. As shown in the output, NMAP identifies a large number of open ports and even identifies the device through information exchanged by the ports.
Figure 2: The image shows a sample port scan of a local printer. (Source: Author)
NMAP is a key tool for network exploration and discovery. Once you understand the attack surface of a network device, you are ready to test the potential exploits on the device.
Testing Potential Exploits on the Device
Understanding whether the network attack vectors of a device include potential exploits is the next phase of penetration testing. Exploit testing is a complicated endeavor, but the Metasploit project simplifies this process.
Metasploit Project
Metasploit is a project that creates a framework for pen testing by supporting exploit matching, execution, and development. Metasploit includes an extensive database of exploits—a small number is shown in Figure 3—which can be matched against a network device under test and then invoked.
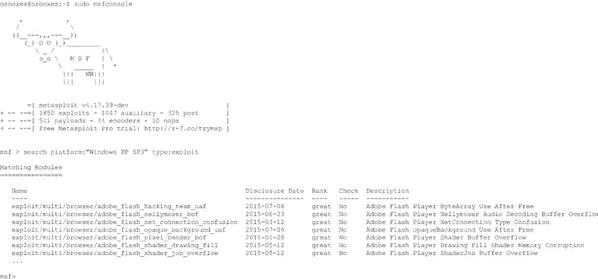
Figure 3: Image of a Metasploit console and a list of XP exploits. (Source: Author)
Metasploit includes shellcode exploits for taking control of a target device by executing code via a payload on the target. Metasploit permits the penetration tester to mix exploits with any payload based upon the fingerprinting of a device and an understanding of its available attack vectors.
The Metasploit framework is the most widely used framework for penetration testing providing a complete environment for discovery, exploit matching, and execution as well as exploit development.
Kali Linux
Finally, there’s a Linux distribution focused on penetration testing and developed by Offensive Security Ltd. Kali Linux, derived from Debian Linux, can be installed on a relatively resource-constrained computer or booted from a CD/DVD or a USB stick. It comes pre-installed with over 600 security testing tools including NMAP, the Metasploit framework, application security scanners, Wireshark (for packet analysis), software suites for wireless LAN pen testing, and many more. Kali Linux even runs on ARM-based devices (such as the Raspberry Pi2) and Android PDA devices (like the Gemini PDA).
Protecting your Devices
While security is commonly an afterthought in device design, there are some basic things you can do to protect your edge devices. Begin by addressing these questions.
- Has the attack surface of the device been reviewed and minimized?
- Are all open ports necessary, or can they be closed after development is complete?
- If you’re running Linux on your device, are the kernel and the packages up-to-date and vulnerabilities understood (such as advertised through the Exploit Database)?
- Has your code been reviewed (either manually or through a source code analysis tool)?
These are basic things that a developer can do to protect their device, but it all begins with an understanding of the attack surface and pen testing.
Conclusion
Penetration testing is based on the idea that to defend your network device in the field; you first need to think about its security offensively. Penetration testing places you in the role of someone who wants to exploit your device so that when your device is released, you can have confidence that you’ve covered known exploits for your OS or network stack.
